Now that decentralized systems are common, blockchain security has become a main concern for companies and developers worldwide. Among other things, blockchain technology is reshaping the process of handling and exchanging data, including smart contracts, dApps, NFTs, and enterprise ledgers. As the decentralized movement progresses, the level of cyber threats against blockchains is also going up. If security strategies are weak, the chance for huge financial losses, legal challenges, and a damaged reputation increases.
Since we are seeing an increase in blockchain use in various businesses, focusing on security in these decentralized spaces is necessary. Blockchain security also involves keeping trust, meeting compliance standards, and safeguarding the entire digital environment. In this blog, we will discuss the importance of securing blockchain data, speak about real cases where things went wrong, and present steps businesses can follow to safeguard their system.
What is Blockchain Security?
The main idea of blockchain security is to fully minimize risks in blockchain networks, apps, contracts and user interfaces. Blockchain security systems must address decentralization, the fact that records cannot be changed and full visibility. The main objective is to guard the network from attackers outside, bugs inside the code, weaknesses in the blockchain protocols and error-ridden smart contracts.
To keep data safe using blockchain technology, cryptography is used together with a distributed system. At the same time, the lack of central control and openness in blockchain can cause security issues, especially where everyone can access and take part.
Why Blockchain Security is Business-Critical
In 2025, the blockchain ecosystem is far more than just a decentralized network for cryptocurrencies. It’s a foundational layer for everything from enterprise logistics and financial systems to Web3 platforms and identity management. Given the irreversible nature of blockchain transactions and the high value at stake, ensuring robust blockchain security is no longer optional—it’s essential.
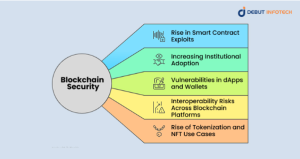
1. Rise in Smart Contract Exploits
When certain conditions are achieved, smart contracts automatically run and conduct the agreed transactions. Although they lower the cost of transfers, they are very tough to keep safe once they’re operational. Any weaknesses in smart contracts are always open to exploitation since they work automatically on the blockchain. An example is the 2016 attack on the DAO which resulted in more than $60 million worth of Ether being taken away through a recursive call bug. As smart contracts are set to function unchangingly, just a minor programming flaw can lead to big losses and ruin reputations. Businesses today are choosing formal tests and independent audits to handle these dangers.
2. Increasing Institutional Adoption
Blockchain technology is no longer limited to crypto-native companies. Enterprises across finance, healthcare, manufacturing, and logistics are incorporating blockchain for security, transparency, and traceability. As these systems scale, compliance with regulatory mandates such as GDPR in Europe or HIPAA in the U.S. becomes non-negotiable. A vulnerability in a blockchain-based identity verification system or financial ledger can expose sensitive data and trigger severe legal consequences. Therefore, robust governance frameworks and end-to-end encryption practices are now central to enterprise blockchain development.
3. Vulnerabilities in dApps and Wallets
Decentralized apps (dApps) and crypto wallets are the gateway between end users and blockchain networks. If these access points are not securely developed and maintained, they become prime targets for phishing attacks, front-end hijacking, and malware injection. Many users have lost their crypto assets due to weak wallet recovery processes or unsecured browser extensions. Security here must go beyond smart contract auditing, including threat modeling, API security, and session management. A holistic approach is required—one that secures both the blockchain backend and its human-centric interface.
4. Interoperability Risks Across Blockchain Platforms
Securing blockchain becomes even more complex as businesses expand into multi-chain ecosystems using bridges or sidechains. Due to weak validation mechanisms, cross-chain bridges have already been targeted in multiple high-profile attacks. Malicious actors can manipulate transactions between chains without strong cryptographic proofs and consensus checks. Companies are turning to trusted blockchain consultants and Web3 development companies to navigate this to establish secure interoperability protocols.
5. Rise of Tokenization and NFT Use Cases
The growing popularity of NFTs and tokenized assets introduces new dimensions of risk. These assets require validation layers, from metadata injection attacks to false ownership claims. Projects without proper blockchain integration for verifying authenticity or tracking ownership lineage face the danger of fraud and counterfeiting. Proper smart contract design, metadata hashing, and secure marketplaces are key to mitigating these risks in token-based business models.
Key Blockchain Threats to Watch
Understanding the threat landscape is the first step toward building a secure blockchain ecosystem. Here are the most common security threats:
- 51% Attacks: Occur when a single entity gains majority control over a network’s computational power, enabling double-spending or transaction censorship.
- Sybil Attacks: Malicious actors create multiple nodes to gain influence in consensus mechanisms.
- Smart Contract Bugs: Coding flaws can be exploited to drain funds or alter logic.
- Routing Attacks: Intercepting data during its transit through Internet Service Providers (ISPs).
- Private Key Theft: Stolen credentials can provide direct access to wallets and assets.
- Flash Loan Attacks: Exploiting blockchain ecosystem protocols with large temporary loans to manipulate market conditions or oracles.
Best Practices for Securing Blockchain Infrastructure
To counteract these threats, organizations must implement a layered approach to security. Here’s how:
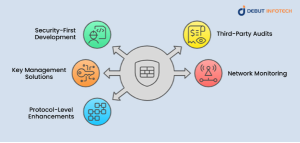
1. Security-First Development
Security should be embedded at every stage of blockchain application development. This includes static and dynamic code analysis, formal verification of smart contracts, and testnet deployment before going live.
2. Third-Party Audits
Partnering with reputable blockchain security firms to audit smart contracts and infrastructure is crucial. Third-party audits catch blind spots internal teams might overlook.
3. Key Management Solutions
Implement multi-signature wallets, hardware wallets, and key rotation policies to secure access credentials. Never store private keys in plain text or within code repositories.
4. Network Monitoring
Real-time monitoring tools and anomaly detection can alert developers to suspicious activity before it escalates into a breach. This includes monitoring node performance, transaction patterns, and access logs.
5. Protocol-Level Enhancements
Choose blockchain platforms that support modular upgrades and implement robust consensus mechanisms like Proof-of-Stake (PoS) or Proof-of-Authority (PoA) that are less vulnerable to brute-force attacks.
Blockchain Use Cases Where Security is Paramount
Financial Services
From crypto exchanges to DeFi platforms, financial institutions are high-value targets for hackers. Securing transactions, wallets, and user data is fundamental to maintaining user trust.
Supply Chain
Enterprise blockchain development is increasingly used to verify the authenticity of goods, track inventory, and ensure compliance. Blockchain security here ensures that data cannot be manipulated to enable fraud or theft.
Healthcare
Sensitive medical records are increasingly being stored on blockchains. Ensuring encryption, access control, and data integrity is critical in this highly regulated sector.
Government and Identity
Decentralized identity (DID) systems built on blockchain must guard against data leaks and ensure biometric and ID data isn’t tampered with or duplicated.
Key Components of a Secure Blockchain Architecture
- Consensus Mechanism: Proof-of-Stake (PoS), Practical Byzantine Fault Tolerance (PBFT), and Delegated PoS are safer than Proof-of-Work in certain environments.
- Encryption Standards: Using SHA-256, elliptic curve cryptography, and advanced hash algorithms to safeguard data.
- Smart Contract Management: Using secure frameworks like OpenZeppelin to minimize vulnerabilities.
- Node Security: Firewalls, VPNs, and endpoint detection solutions to protect the underlying node infrastructure.
- Governance Protocols: Well-defined roles and permissions prevent unauthorized changes or interventions.
Blockchain Security and Compliance
For businesses, ensuring blockchain security also means staying compliant with various international standards and data privacy laws. Consider these:
- ISO/IEC 27001 for information security management
- GDPR for data handling and processing
- SOC 2 Type II for system and data protection
By integrating compliance, blockchain business development reduces the risk of fines, breaches, and customer churn.
How Debut Infotech Helps Secure Your Blockchain Projects
At Debut Infotech, we understand that security is not optional—it’s essential. As a leading web3 development company and provider of blockchain development services, our approach ensures your blockchain project is not only functional but fortified against evolving threats.
Whether you’re exploring Ethereum blockchain development, launching enterprise blockchain solutions, or building decentralized apps (dApps), we provide:
- Blockchain Security Audits
- Custom smart contract development with formal verification
- Compliance-ready architecture
- Ongoing vulnerability assessments
- Blockchain integration and deployment strategies
Our dedicated software development team brings years of industry experience and leverages best-in-class frameworks to safeguard your project at every stage.
The Cost of Insecurity: What Blockchain Breaches Really Cost
According to Chainalysis, over $3.8 billion in crypto was stolen through blockchain exploits in 2022 alone. The blockchain development cost may be an investment upfront, but security oversights can lead to financial devastation, legal implications, and loss of market trust. Being proactive isn’t just about prevention—it’s about survival in a competitive, decentralized world.
Conclusion
Blockchain security isn’t just a technical requirement—it’s a business imperative. As the world continues to move toward decentralized systems, the importance of proactively securing blockchain applications grows every day. From smart contracts to full-scale enterprise platforms, every component must be safeguarded through a combination of strategy, tools, and expertise.
With the rise of complex blockchain platforms, evolving threats, and expanding blockchain use cases, partnering with the right blockchain consultants is vital. Companies like Debut Infotech help you stay ahead of the curve by offering cutting-edge solutions that integrate trust, scalability, and ironclad security.